VMware NSX Distributed IDS/IPS
Enhancing VMware Service-defined Firewall with advanced threat detection

Overview
What is VMware NSX Distributed IDS/IPS?
NSX Distributed IDS/IPS is an application-aware intrusion detection system/intrusion prevention system (IDS/IPS) purpose-built for analyzing east-west traffic and detecting lateral threat movements.
At A Glance
VMware NSX® Distributed IDS/IPS™ provides security operators with a software-based IDS/IPS solution that enables them to achieve regulatory compliance, create virtual zones and detect lateral movement of threats on east-west traffic.
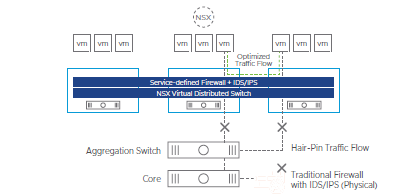
NSX Distributed IDS/IPS eliminates traffic hair-pins
Distributed IDS/IPS breaks traditional security trade-offs
The VMware Service-defined Firewall provides the only purpose-built internal firewall that
secures east-west traffic. It virtualizes and distributes the entire security stack to every
workload and delivers a rich set of firewalling capabilities, including layer 4 access controls
and stateful layer 7 network controls. The Service-defined Firewall’s capabilities now
include an intrusion detection system and intrusion prevention system (IDS/IPS).
IDS/IPS have long been standard capabilities of the network security stack. However,
cost and operational complexity have restricted their use to specific network segments,
at the enterprise perimeter to public networks or at the boundaries of regulatory
compliance zones.
VMware NSX Distributed IDS/IPS offers a fundamentally new architecture that breaks this
traditional trade-off between breadth of security coverage and operational complexity.
It embraces an all-software distributed approach, moving traffic inspection out to every
workload and eliminating the need to hair-pin traffic to discrete appliances. The operational
simplicity of deploying and managing IDS/IPS functionality at each workload ensures
comprehensive coverage without any blind spots
Features
Application context-driven threat detection
The IDS/IPS engine has definitive knowledge of applications running on each host, eliminating guesswork regarding the source or target application context. This knowledge allows for better alert classification and operator ability to prioritize alerts for further investigation.
Curated, context-based signature distribution
The management plane enables only the relevant threat signatures for evaluation at each workload based on knowledge of the running applications. This reduces computational overhead on the host and results in higher fidelity matches with lower false positive rates.
Automated policy lifecycle management
The NSX policy model enables the automatic creation of security policies for new workloads and the tear down of old policies when workloads are decommissioned. Security policies remain consistent with deployed workloads, preventing the accumulation of stale policies, a common challenge with traditional network security appliances.
Distributed analysis
The IDS/IPS engine is distributed out to each workload, eliminating blind spots while maintaining a simple operational model. The inspection capacity scales linearly with the number of workloads, eliminating the throughput constraints typically experienced with discrete appliances.
Policy and state mobility
When workloads move, the policies and the state move with the workload. Workloads are automatically secured at their new location without manual configuration or dropped flows.
Key Benefits:
Elastic throughput – Eliminate hardware bottlenecks with inspection capacity that scales automatically with each workloa
-
Simplified network architecture –Avoid the need to hair-pin traffic to centralized appliances, and reduce network congestion with a fully distributed architecture.
-
Improve capacity utilization –Reuse existing stranded compute capacity, eliminating the need for dedicated appliances.
-
Reduce false positives – Enjoy more zero false positive workloads with curated rule sets and higher fidelity signature matches based on the precise application context.
Use Cases:
The Growing Need for East-West Threat Detection
With the rise of distributed applications and microservices, internal network traffic now dominates traditional north-south traffic. At the same time, the data center boundary has diffused with edge and cloud applications as well as with end-user devices. Modern-day attackers noticed these changes and learned to move laterally, aggressively, from their initial point of attack. As a result, inspecting internal east-west (server-to-server) traffic with an advanced threat detection capability is increasingly critical to securing workloads and enterprise data.
Use Cases
Easily achieve regulatory compliance – Turn on traffic inspection for sensitive applications by deploying software without needing to buy expensive appliances.
Virtualize security zones – Create and customize multiple virtual security zones for internal teams and partners without requiring physical separation of the network.
Replace discrete appliances – Leverage IDS/IPS capabilities native to NSX to replace traditional IDS/IPS appliances, reducing cost and complexity.
Detect lateral movement of threats – Inspect east-west traffic at each workload using signature-based techniques, anomaly-based detection and protocol conformance checks
Datasheets
Download the Solution Overview (PDF).

